Vulnerability Management Plan Template - Identifying threats to and vulnerabilities in the system; Web we've created a vulnerability management policy template to help organizations assess and patch security vulnerabilities. While we strive to keep the information up to date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability, or. Web security patch management team members. A detailed methodology for calculating the risk posed by software vulnerabilities. Web completing the scope task, you should be able to explain to your management and your peers why vulnerability testing is needed and how it benefits the business. You'll also be subscribed to deploy securely. List weaknesses to be addressed along with remediation plans, deadlines and milestones, risk levels, and status updates. Establish a list of assets that need protection. Define the criticality of each asset.
Vulnerability Management Process Template
Web vulnerability management policy template. Web security patch management team members. A comprehensive guide for systematic detection, mitigation, and review of risks. Web we've created.
Vulnerability Management PowerPoint Template SketchBubble
As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for. You should be able to outline.
Vulnerability Management Policy Template
Montana currently participates in the cisa cyber hygiene services including vulnerability scanning of our external facing network assets. Web this guide is intended for organizations.
Vulnerability Management Policy Template
To help you get started creating a policy for your organization, we’ve created a customizable template that you can download below. Identify all systems, applications.
Amazing Vulnerability Management Policy Template Sparklingstemware
Web this guide is intended for organizations seeking help in establishing a vulnerability management process. Web the guide provides in depth coverage of the full.
Vulnerability Assessment Plan Template in Word, Pages, Google Docs
A comprehensive guide for systematic detection, mitigation, and review of risks. Web understanding and managing vulnerabilities is a continuous activity, requiring focus of time, attention,.
Vulnerability Reporting Template
Montana currently participates in the cisa cyber hygiene services including vulnerability scanning of our external facing network assets. Determining the likelihood and magnitude of harm.
14+ Vulnerability Assessment Templates PDF, DOC, Pages
Reduce the prevalence and impact of vulnerabilities and exploitable conditions across enterprises and technologies, including through assessments and coordinated disclosure of vulnerabilities reported by trusted.
Vulnerability Assessment Plan Template in Word, Pages, Google Docs
Web free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. Web free vulnerability management policy template. This policy.
You Should Be Able To Outline The Next Steps.
Reduce the prevalence and impact of vulnerabilities and exploitable conditions across enterprises and technologies, including through assessments and coordinated disclosure of vulnerabilities reported by trusted partners. List weaknesses to be addressed along with remediation plans, deadlines and milestones, risk levels, and status updates. Web conduct a risk assessment, including: As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for.
Web Vulnerability Management Policy Template.
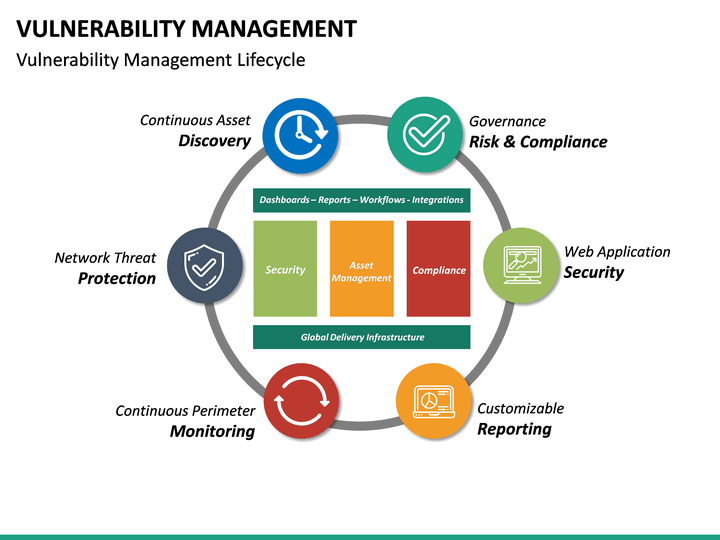
Easily track and manage objectives with. Web the guide provides in depth coverage of the full vulnerability management lifecycle including the preparation phase, the vulnerability identification/scanning phase, the reporting phase, and remediation phase. Web completing the scope task, you should be able to explain to your management and your peers why vulnerability testing is needed and how it benefits the business. Web this guide is intended for organizations seeking help in establishing a vulnerability management process.
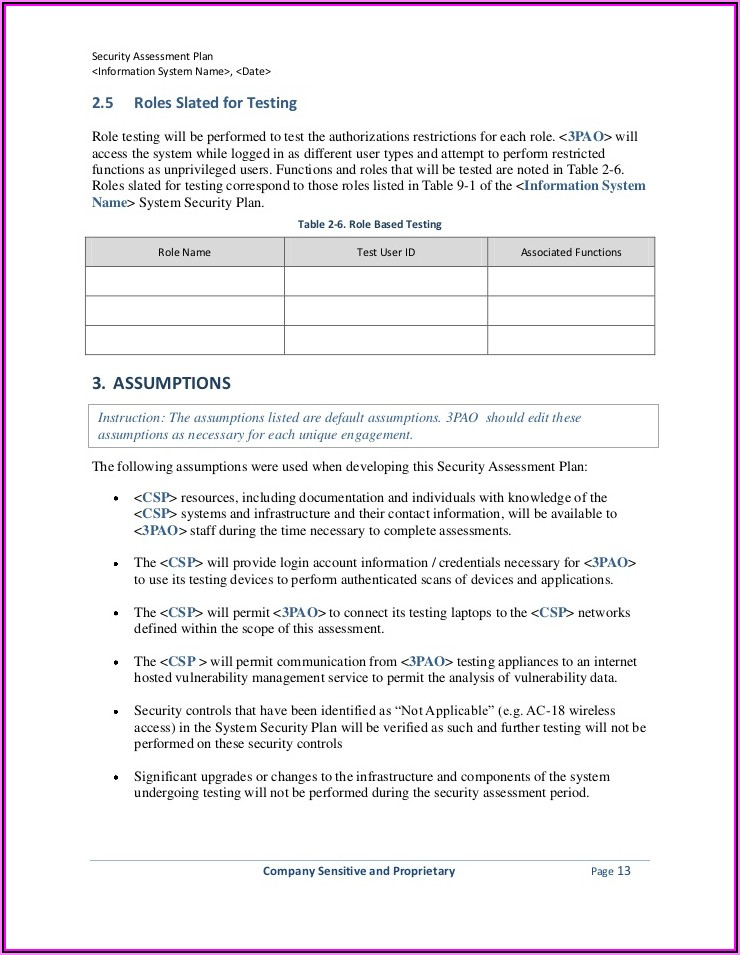
Identify All Systems, Applications And Data To Be Assessed.
Web the sans vulnerability management maturity model helps you gauge the effectiveness of your vulnerability management program. Web evaluate the current level of security risk and create a plan for reducing or eliminating it. Web create a vulnerability assessment action plan template that focuses on remediation. Determining the likelihood and magnitude of harm from unauthorized access, use, disclosure, disruption, modification, or destruction of the system, the information it processes, stores, or transmits, and any related information;
A Detailed Methodology For Calculating The Risk Posed By Software Vulnerabilities.
Identify key performance indicators (kpis) for tracking the progress of the vulnerability management process. You'll also be subscribed to deploy securely. Web free threat & vulnerability management templates for organizations to effectively identify and mitigate security risks internally. To help you get started creating a policy for your organization, we’ve created a customizable template that you can download below.