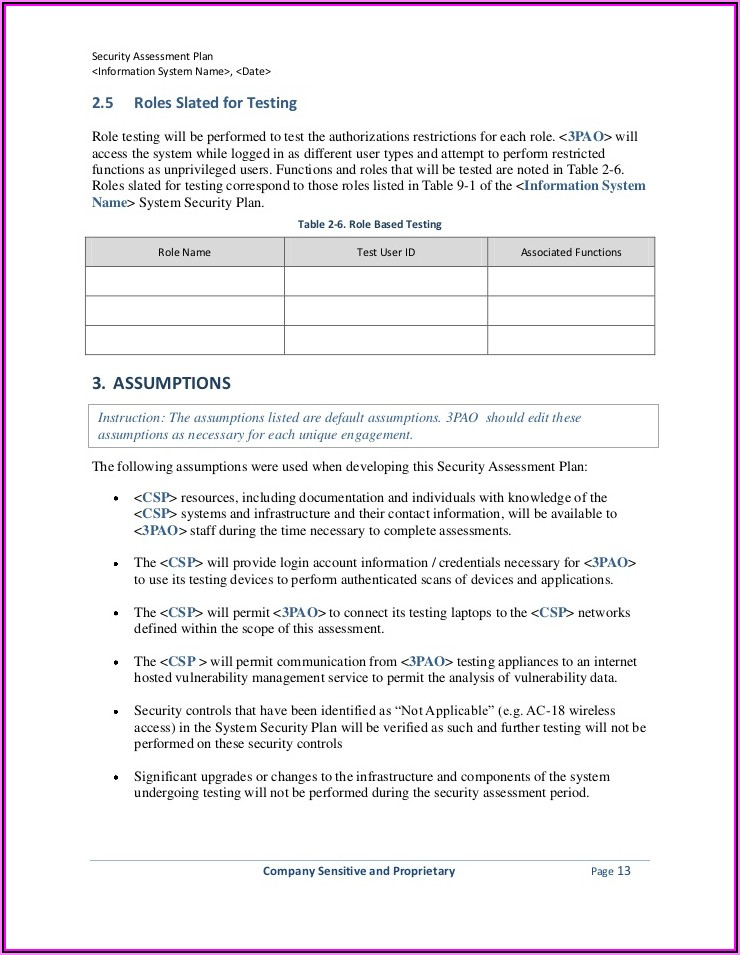
Vulnerability Management Policy Template - The official web page of the ovmg contains a gif animation that illustrates connections among all tasks in the tricycle. Explain how the vulnerability management policy will be enforced. Outline the process for identifying, scoring, and mitigating vulnerabilities. To help you get started creating a policy for your organization, we’ve created a customizable template that you can download below. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for. States the policy’s objectives and defines the areas covered by the policy. Web free vulnerability management policy template. Define your approach for vulnerability management to reduce system risks and integrate with patch management. 4.5/5 (7,518 reviews) Web use this template to:
Vulnerability Management Process Template
Elaborates on specific policy aspects. In the identification stage, teams must scan all devices and environments to detect vulnerabilities. Web use this template to: Web.
Vulnerability Management Policy Template in 2021 Patch management
Elaborates on specific policy aspects. Discusses compliance requirements and procedures. Web vulnerability management policy template google docs. Web download free, customizable vulnerability assessment templates, available.
Amazing Vulnerability Management Policy Template Sparklingstemware
Elaborates on specific policy aspects. Outline the process for identifying, scoring, and mitigating vulnerabilities. Discusses compliance requirements and procedures. As both an example and a.
Vulnerability Management Policy Template for CIS Control 7
Web a vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls. States the policy’s objectives.
Free Vulnerability Assessment Templates Smartsheet
In the identification stage, teams must scan all devices and environments to detect vulnerabilities. Outline the process for identifying, scoring, and mitigating vulnerabilities. Web free.
Vulnerability Management Policy Template Nist
This requires a number of automated scanning tools for the various it environments and phases. Discusses compliance requirements and procedures. Web the cyclical nature of.
Vulnerability Assessment Template Download Printable PDF Templateroller
To help you get started creating a policy for your organization, we’ve created a customizable template that you can download below. Define your approach for.
Vulnerability Management Policy Template for CIS Control 7
Web the cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes.
Vulnerability Management Policy PDF Vulnerability
Identifies responsibilities of different roles. Web we've created a vulnerability management policy template to help organizations assess and patch security vulnerabilities. Web free vulnerability management.
Identifies Responsibilities Of Different Roles.
Web free vulnerability management policy template. Web we've created a vulnerability management policy template to help organizations assess and patch security vulnerabilities. As both an example and a starting point, esecurity planet has developed a free vulnerability management policy template for. In the identification stage, teams must scan all devices and environments to detect vulnerabilities.
Web Use This Template To:
States the policy’s objectives and defines the areas covered by the policy. Web vulnerability management policy template google docs. Web download free, customizable vulnerability assessment templates, available in excel, word, pdf, and google sheets formats. Web a vulnerability management policy defines an approach for vulnerability management to reduce system risks and processes to incorporate security controls.
This Requires A Number Of Automated Scanning Tools For The Various It Environments And Phases.
4.5/5 (7,518 reviews) Discusses compliance requirements and procedures. The official web page of the ovmg contains a gif animation that illustrates connections among all tasks in the tricycle. Elaborates on specific policy aspects.
Explain How The Vulnerability Management Policy Will Be Enforced.
Web the cyclical nature of vulnerability management implies continuous process improvement, and it is crucial to understand how a single process feeds into other processes and how all tasks are interconnected across three domains. Web experience effective it asset management with our vulnerability management policy template, ensuring risk evaluation, strategic planning and continuous improvement. Outline the process for identifying, scoring, and mitigating vulnerabilities. Define your approach for vulnerability management to reduce system risks and integrate with patch management.